Cybersecurity Awareness Month: Why It Matters A Q&A information session with Chief Information Officer David Saacke.
Cybersecurity remains a threat to both individuals and institutions around the world. In 2004, U.S. Congress and former president George W. Bush declared the month of October to be Cybersecurity Awareness Month, a dedicated month for the public and private sectors to work together to raise awareness about its importance.
In recognition of this initiative, David Saacke, W&L’s chief information officer, participated in a Q&A session related to the university’s efforts to protect the campus from these threats.
What are some of the actions the university’s Information Technology Services (ITS) organization takes to enhance protection of W&L’s technology network?
While ITS has employed a component of cybersecurity for some time, the explosion of cyberattacks and compromises led ITS to formalize W&L’s security program almost 10 years ago. The intent was to adopt a best practice framework for managing the cybersecurity program, dedicate resources to the effort, and deploy higher-grade protective tools and services. Since then, we’ve been employing industry standard intrusion detection tools and performing ongoing maintenance upgrades on W&L’s technology infrastructure.
Recently, the biggest step we’ve taken is to address and improve the campus community’s awareness. This effort includes proactive training for all new campus members, monthly simulated phishing tests, and follow-up training for those struggling to identify phishing emails. It’s important for all W&L technology users to know that the most common method used by cybercriminals to gain access to our systems is to take advantage of mistakes made by individuals interacting with phishing messages.
How has the evolution of phishing emails made it harder to detect those cyber threats
Phishing messages don’t always arrive as massive blasts of poorly constructed emails attempting to find a way past our filters, as was frequently the case in the past. They now arrive more inconspicuously in small batches containing highly targeted information about employees or students, making them look less “phish-like.” The industry refers to this method as “spear phishing,” with the use of social engineering. The recent boom of access to artificial intelligence (AI) tools has increased the sophistication and “realness” of phishing attempts. Unfortunately, industry security professionals warn that evolving phishing techniques will become much more difficult to distinguish from legitimate email as AI advances over time.
How often is ITS faced with compromised W&L user accounts requiring immediate mitigation?
In 2020, W&L averaged four compromised university accounts every month. When an account is compromised, it means the hacker has tricked user into revealing their W&L username and password, allowing them to gain full control of all the university systems that particular user routinely logs into. While the cyber threats have intensified in recent years, we’ve seen a reduction in compromised accounts the past couple of years. We believe our security measures have helped on this front.
We’ve added multi-factor authentication (Duo) to our network login process. We’ve woven a single sign-on solution (Okta, otherwise known as the W&L MyApps page) into application access and implemented Advanced Threat Protection from Microsoft to warn users about suspicious emails. We’ve also made passphrases a requirement of network credentialing because they’re much harder to crack.
As of October 2023, we’re averaging about 1.5 compromised W&L accounts per month. Many more account credentials are inadvertently shared by falling prey to phishing attempts, but with the protection of Duo, the attacker was unable to leverage access to W&L systems using those credentials.
With all the protections in place, how are cybercriminals still able to break into networks?
Protecting a technology environment will always be a “cat and mouse” paradigm where advances in protection tools and techniques create a new baseline challenge for those developing sophisticated intrusion methods. That’s why best practice security models do not rely on one tool or process, instead employing a layering effect of several tools and processes to create holistic security around the institution’s assets. Even then, risks exist and compromises can occur. The strategy is to lower your risk and exposure to the degree possible knowing that both will always be present. The last line of defense is the individual user when it comes to preventing unauthorized access. Cybercriminals also know this, and they’ve made it more difficult for the individual to recognize when a scam is taking place.
What are some techniques cybercriminals are using to fool technology users?
Scammers will often take advantage of seasonal messaging to camouflage their intentions. For example, during the holiday shopping season, they know there’s a high probability you may have placed online orders requiring package delivery. In this case, the criminals may send you an SMS text or email telling you a package is inbound, with a link to track the package. They will convey a sense of urgency by asking you to “confirm an order or it will be returned,” or that you might be charged for something you didn’t order. Clicking the link can infect your device with malware, or it may direct you to a form that collects your personal information or even banking information.
Cybercriminals are also now using techniques to imitate the legitimate credentialing process specific to a particular university. For example, if an individual gets tricked into clicking on a link in a phishing email, they can be redirected to a page that may look exactly like a W&L login page, but in reality is hosted on a malicious website. When coupled with a request on the page for a Duo code, the W&L user’s account is now successfully compromised and access to the systems available to the user have become available to the attacker.
What is the biggest cyber threat facing higher education institutions?
The biggest cyber threat for colleges and universities today is that a compromised account leads to the disabling or destruction of critical systems and may result in a ransomware scenario. Based upon recent ransomware events seen at other universities, the downtime for this type of incident averages around 16 days. It would mean a complete halt to most of the essential daily functions of the university because all the network resources would need to be shut down. It’s been estimated that remediation from a ransomware attack costs educational institutions an average of $2.5 million. The impact and ramifications of a ransomware attack are huge — it should not be taken for granted that an incident could occur at W&L.
What role do W&L technology users play in the university’s cybersecurity defense?
Each W&L employee and student plays a crucial role in protecting our community and should be vigilant in their use of technology tools. An overused analogy I often mention is to consider how you handle similar non-technology scenarios, such as when you travel to a strange city and are in your hotel room. If you hear a loud knock at your door, do you simply open it without a thought of who or what is on the other side? Likely, you first look out the peephole, then ask the person at the door to identify themselves. Employ this same logic to any email you receive or site requesting information from you. Who is it? How can you be sure it’s who you think it is? Must you click on the link, or is there another way to navigate to the same website but through your bookmarks or other tools like a password manager? Because of the email volume we receive daily, it’s tiresome to do this with every email. But like wearing a seatbelt in a car, the more you intentionally scrutinize your messages, the more normal the habit becomes.
Who should students and employees contact if they have questions related to cybersecurity?
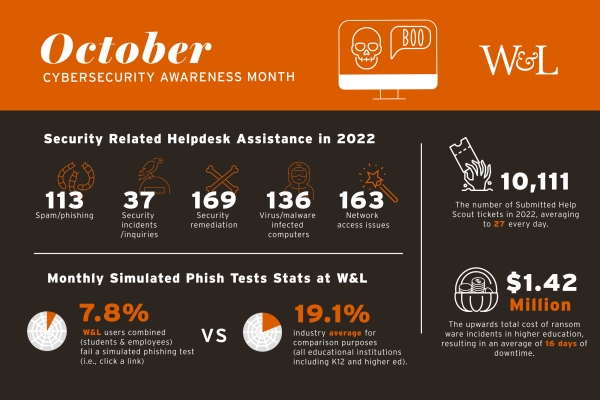
The best place to start is the ITS Helpdesk. The Helpdesk staff is knowledgeable and efficient in connecting you with the resources, solutions and personnel to get your issues or questions resolved quickly. Last year, the Helpdesk worked to resolve 10,111 questions or tickets that came into the Web Help Desk system. Of those, 618 involved security-related assistance, which included spam/phishing events, security inquiries, security remediation, software updates, infected computers, and login or password issues.
What should a W&L user do if they think they’ve received a phishing email?
If you receive a suspicious email, even if you’re unsure, click the Phish Alert Button in your Outlook email platform. The button is available to all W&L students and employees and can be found in both W&L Outlook web and client apps for Windows and Mac users. The Phish Alert Button is also on the mobile Outlook app on Android and iOS. There’s no risk of losing important emails if you click the button accidentally; you can always go retrieve the email from your deleted folder. Not an Outlook fan? No problem — simply forward the suspected phishing email as an attachment to phish@wlu.edu and it will be processed the same way as using the Phish Alert Button.
Are there any recent cybersecurity-related trends ITS is seeing that the community should be aware of?
Over the past year, we’ve seen a rise in a new strategy called MFA fatigue attacks. In fact, they’ve been successful enough to cause a short-term rise in compromised accounts here at W&L. They work by literally “fatiguing” the user by sending dozens of Duo push requests to someone’s phone or network-connected device, over and over. The goal is to frustrate the user until they “give in” and approve the Duo request. Once that happens, the attacker is given immediate access to that user’s account and all their university network privileges.
To combat this type of cyberattack, Duo will be ending support for its traditional MFA method where users simply “Approve” the request. Instead, Duo is moving to a new type of prompt that, in most cases, should help to prevent fatigue attacks. ITS has been testing this new authentication method over the past couple of months. It will require an extra click when logging in on campus and will require the user to occasionally enter a three-digit code when off campus. The enhanced security should present very little friction to W&L users overall. ITS plans to roll out this new defense in the second week of November and will update the university community about the change through Campus Notices and in an upcoming detailed communication.

You must be logged in to post a comment.